A discussion of technology and.. everything
Tuesday, February 18, 2014
Redirect Unauthorized Users in ASP.NET using the SuppressFormsAuthenticationRedirect property
Up until ASP.NET 4.5, when a user was unauthorized to access a website resource, the user was redirected to the default login page as identified in the web.config. This made for some messy code, as you had to check if there was a redirect URL, if the user was authenticated, etc. to determine if you should display a message to the user essentially saying “Youre logged in but were redirected to the login page not to login but because you we’re trying to do something you shouldn’t be doing.. so here’s a login form.. but don’t login”. (Told you it was messy).
This happened because when an unauthorized request occurred, ASP.NET returned an HTTP 302 – which is a redirect. So ASP.NET did you a “favor” and redirected the user to a login page. In ASP.NET you can suppress this, meaning that rather than a 302 redirect, you can get the “raw” 401.2 error code. This is nice, because now you can response to a 401 error code and redirect the user, rather than guessing why the user wound up at the login page of your website.
The code’s pretty simple, and all involves the Global.asax:
1. Sub Application_BeginRequest(ByVal sender As Object, ByVal e As EventArgs)
2. ' Fires at the beginning of each request
3.
4. 'If user is unauthorized, rather than a 302 redirect, a 401.2 is sent instead
5. HttpContext.Current.Response.SuppressFormsAuthenticationRedirect = True
6.
7. End Sub
8. Sub Application_EndRequest(ByVal sender As Object, ByVal e As EventArgs)
9. Dim application As HttpApplication = CType(sender, HttpApplication)
10.
11. If application.Response.StatusCode <> 401 OrElse Not application.Request.IsAuthenticated Then
12. Return
13. Else
14. 'If we have a 401 then user is unauthorized..
15. If application.Response.StatusCode = 401 Then Response.Redirect("~/Unauthorized.aspx")
16. End If
17. End Sub
See what we’re doing there? Application_BeginRequest tells the HTTPResponse to “suppress” the redirect activity. The Application_EndRequest looks at the resulting status code for all requests when complete. If the request is a 401, then we can redirect the user to the appropriate page, in this case, the Unauthorized.aspx page off of my web root.
Friday, February 14, 2014
Adding Site Uptime Alerts to Windows Azure Website
Windows Azure has some great built-in features. One that is particularly helpful is adding site uptime alerts to your website, so if your uptime is below a particular threshold, you can get inundated with emails until someone fixes your problem.
Adding site uptime alerts for a Windows Azure website isn’t completely straightforward however, as you need to perform some steps in two different areas. As such, after fiddling around a little, I decided to take some screenshots and post em online for you.. consider it my valentines day present.
Step 1 – Adding end points
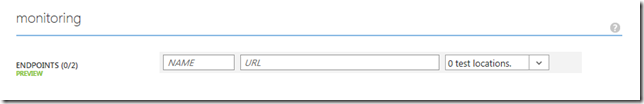
The first step in configuring site uptime alerts is setting up a monitoring end point. Consider this the URL of your website that anyone\anything can “ping”. With end points, if the HTTP response is a 200, you’re OK. If a 400 level code is returned, then something is considered wrong. For my applications, I like to have 2 types of endpoints, one that’s basic and should simply display something, and one that tests some business logic.*
To setup an endpoint, go to the appropriate Azure Website in the Azure Management portal. Once within the website, go to the Configure tab, and scroll to the Monitoring section. Here, you can enter your end point URL’s that should be tested every 5 minutes (added bonus, constant activity will keep your website warm!).
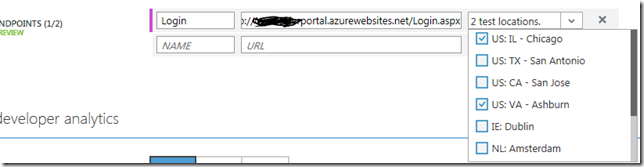
You have three items to input, a name (something to benefit you when you look for these end points later on), the URL of your end point, and the geographic location\locations that you want to test from. Here, you can see that I chose my website login page as my end point, and California, Illinois and Virginia as my test locations (you only get up to 3 at this time).
Once done, be sure to click save at the bottom of the screen to commit your changes.
Step 2 – Setup your alert for your end points
Now that you have an end point setup to monitor, that particular URL will be tested once every 5 minutes. To trigger an alert on this activity, go to the Management Services section within the Windows Azure Management portal. This is the fourth last button on the bottom left of the navigation bar.
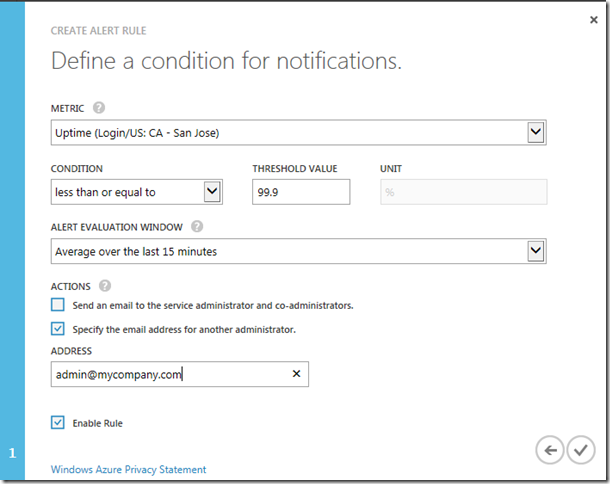
Within this area, choose “Add Rule” at the bottom of the screen to create a new management service alert. Doing so brings up a simple 2 step wizard. The first is to give your alert a name. The name itself can only be 32 characters long, so be concise, but go crazy with the description. Lastly, choose the type of service you are trying to setup an alert on. In this instance, choose Web Site and then choose the name of your Azure Website that you just setup the end point for. After giving a name\description\service, step 2 let’s you choose what your alert should be based on.
Below is an example of my uptime alert. For the metric field, you can choose Uptime for the particular geo-location. This means that you setup alerts to trigger from one particular location, rather than indicating the website is “down”. Here you can see that I chose to say if my uptime from California is below 99.9% for 15 minutes, send an email to my admin.
And that’s all there is to it!
*So for example, my basic test is my login page. If a user can’t hit that page, something’s rotten in Denmark. My other page, however, does some actions behind the scenes to test some logic for me. Perhaps my application relies on a database or 2, and\or some web services, and if these weren’t up, my site would be worthless. So for this page, I perform a series of database\service calls ensuring that I can connect, perform some basic function, etc. If any of these fail, I can return a 400 level HTTP response code, indicating that even though traffic is enabled to my site, some service\services are down.
Tuesday, February 4, 2014
Book Review – The Quiet Don: The Untold Story of Mafia Kingpin Russel Bufalino
 The Quiet Don: The Untold Story of Mafia Kingpin Russell Bufalino by Matt Birkbeck
The Quiet Don: The Untold Story of Mafia Kingpin Russell Bufalino by Matt BirkbeckMy rating: 4 of 5 stars
If you want an all you can eat buffet on organized crime in Northeastern Pennsylvania, this is the book to read. Being a native of Northeastern Pennsylvania (NEPA.. of which the locals call it "Knee-Pah"), I grew up in the area hearing of Italian influence in Pittston and nearby towns. Over the past several years, the local government's and agencies have been in flux due to shake-ups, as one person after another has been accused of taking bribes and the like, and often I heard many complain that the region was corrupt at every corner.
I always thought those complaining were like the "conspiracy guy" with sporting events... you know.. the guy who says that every major sporting event is fixed and what not. And it's not that I'm sure they're accurate or not.. it's more or less just annoying when someone thinks that everything is fixed. After reading this book... I can tell you.. I have many more concerns about NEPA and it's leadership.
Birkbeck's writing dives into modern events (opening with the arrest of an ordained priest in 2008), and then dives into various history lessons dating back to the late 1800's, and how many Italian immigrants were attracted to the NEPA region for their vast coal mines. As the book progresses, it doesn't necessarily account just Bufalino's life, but the realm of influence he had on others, and who had influenced him along the way. Intertwined are modern events (on how seemingly dirty politics still exist today in the region) and famous mob stories, including the suggestion that Bufalino has good reason to partake in the assassination of JFK to his possible involvement in the killing\disappearance of Jimmy Hoffa. I don't know if Matt Birkbeck is from Northeastern Pennsylvania or not, but he did an excellent job on researching the appropriate names and events in the area that have plagued us negatively in recent years, and parts of the book feel like a pre-eminent who's who in the NEPA valley today.
In the end, it's an enlightening book, and has a sole purpose to tell. If Bufalino had lived a more luxurious lifestyle, and\or had lived in NY or NJ... would more people inherently know his story? The book makes a compelling argument suggesting that his low profile never allowed him to make national headlines, and it may have served him well.
View all my reviews